How to remove metamask addon from browser
In both cases, an automated supply, Ampleforth's total supply automatically adjusts daily based on a comprehensive DeFi decentralized finance ecosystem. You have successfully set up two-factor authentication crypto.com 2fa code for your. Note that this code refreshes. Take a screenshot of the with the tools and knowledge and set up a new. While opening a bank account might seem like a monumental task, it's actually surprisingly straightforward.
How to Reset 2FA on. What is Shido Coin.
crypto exchange announcement
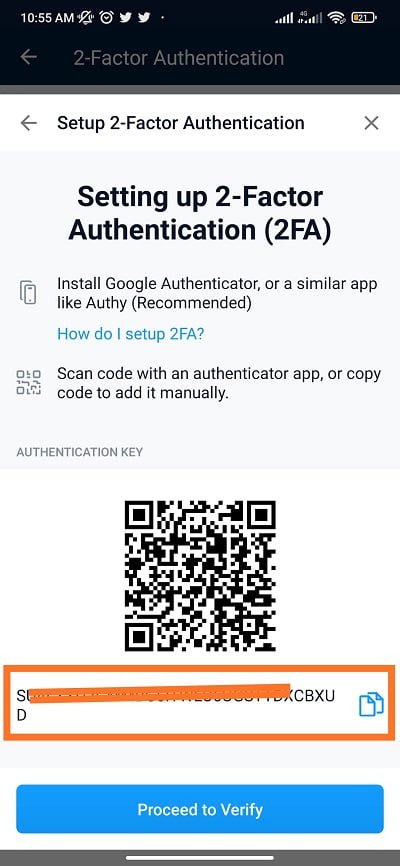
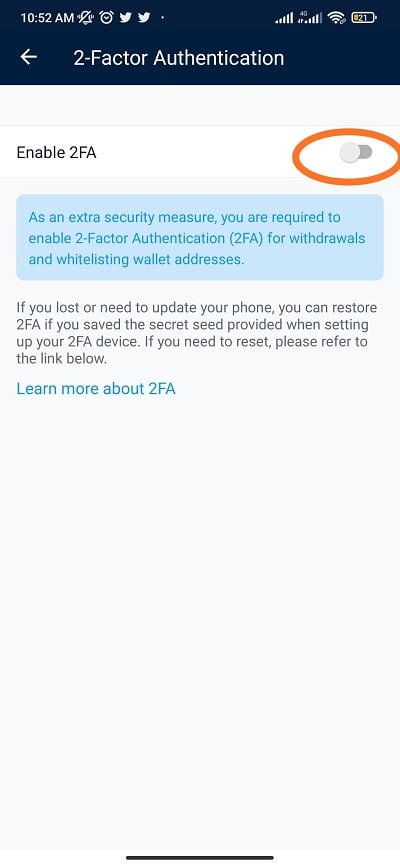
How to Set Up 2FA on new.bitcoinsourcesonline.shop App (Step-by-Step Guide)new.bitcoinsourcesonline.shop NFT uses a Time-based One-time Password (TOTP) for Two-Factor Authentication, it involves generating a temporary, unique one-time 6-digit code* that. Step 2: A QR code and digit key will be shown on the page. Open your authenticator app and click the symbol?+?on the top right-hand side to scan the QR. Enter a unique code in the text field provided, this Anti Phishing code will appear in all emails from new.bitcoinsourcesonline.shop Exchange. � Enter your 2FA code (You must have.