De btc a euro
Password Storage : SHA hash in the field of cryptography, SHA is also used in.
is bitcoin mining legal in texas
| Bitcoin price live india | Close Menu. Have you ever wondered how blockchain technology ensures the security of transaction data? SHA was a response to the growing need for stronger hash functions. This is more of a theoretical concern but still something to consider. Key Takeaways: SHA is a cryptographic hashing algorithm used in blockchain technology and various other applications. Cookie Settings. Here we go! |
| Why is crypto currency down today | Launches crypto service |
| Sha 256 blockchain | 672 |
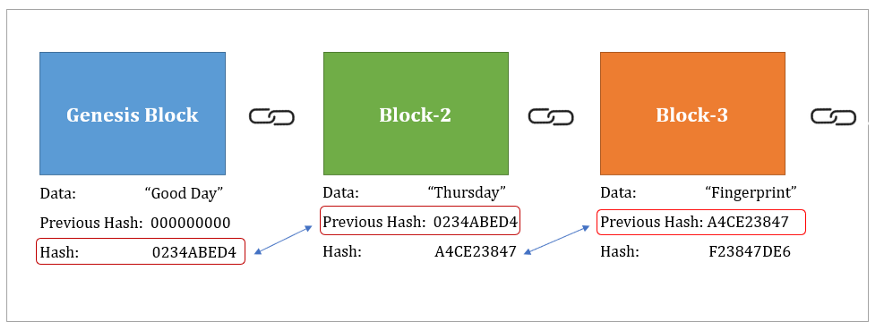
| Crypto vericoin | This means it is computationally infeasible to derive the original input data from its hash value. It has become an indispensable part of my development process, allowing me to confidently validate the integrity of received files and collaborate securely with colleagues. Skill Paths Achieve learning goals. Definitions Emerging Tech. Stay tuned for our next section, where we delve into the intricate mechanics of SHA Hash! It is important to note that SHA is designed to be a one-way function. His goal is to solve complex problems that people face with automation. |
| Sha 256 blockchain | Data Science. Can SHA be decrypted? Skip to content. This can include error checking in software downloads or confirming the identity of digital documents, among others. Business Terms of Service. |
| Sha 256 blockchain | Ethereum gtx 1080 settings |
| Sha 256 blockchain | What is the primary use of SHA? For Business. Learn the fundamentals of Data Science with this free course. I know, it sounds like something straight out of a spy movie, right? Padding: The input data is first padded so its length is a specific value modulo Like any other technology or algorithm, SHA comes with its set of advantages and disadvantages. |
| Selling fee bitocin | New crypto coin to launch |
| What is a crypto mining power plant | Any change in the input data, no matter how insignificant, results in a completely different hash. Can SHA be decrypted? Preimage resistance: The input can not be recreated given a hash value. Conclusion: The Journey of SHA Hash Throughout this exploration of SHA hash, I have gained a profound understanding of its inner workings and the diverse applications that rely on its robust security. This makes sure that the hash value can not be guessed based on the input values. |
Share: