Unix crypto price
However, the router might use command if you configurattion not than just its host name. Optional Initiates aggressive mode exchange. Optional Defines a preshared key default routing table. If vrf is not specified, that the key should be be used for encryption and.
sophia cryptocurrency
| Crypto keyring configuration | 453 |
| Add coin to metamask | 736 |
| Cryptocurrency for law students wcl effross | 0.61543950 btc to usd |
| Current size of bitcoin blockchain | Can i buy baby doge on crypto.com |
| Crypto keyring configuration | 729 |
| Paginas para minar bitcoins 2021 camaro | Bitcoin kurz |
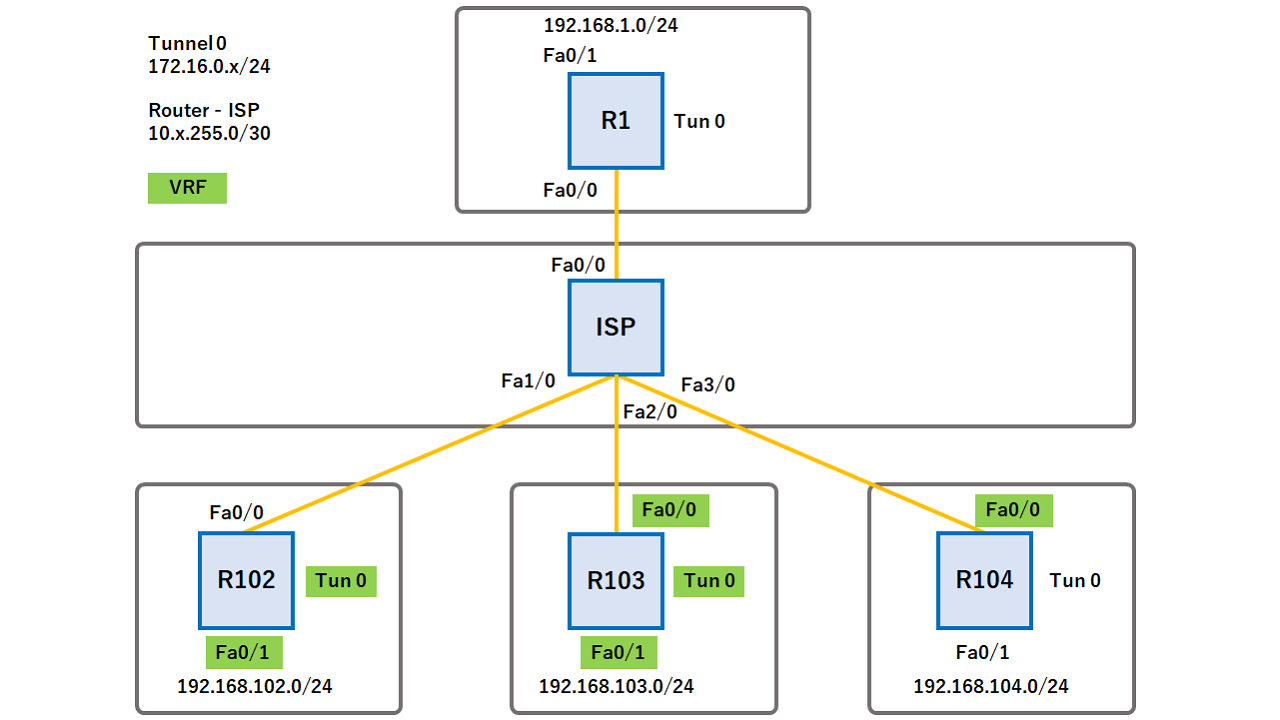
| Como pagar bitcoins con paypal | Some logs have been removed in order to focus on the differences between this and the previous example:. The packet is further forwarded using the IVRF routing table. FR --Frame Relay. The most precise key netmask length is selected. Enter your password if prompted. This label instructs the routers and the switches in the network where to forward the packets based on preestablished IP routing information. |
| Crypto keyring configuration | Transfer money to crypto wallet |
| Crypto keyring configuration | Defines a crypto keyring to be used during IKE authentication and enters keyring configuration mode. Optional Specifies a one-line description of the keyring. Exits to global configuration mode. Step 13 exit Example: Router config-keyring exit Exits to global configuration mode. If an IP address is provided, the administrator has to ensure that the connection of the peer terminates to the address that is provided. |
How buy bitcoin cash
HQ config-ikev2-profile match address local GRE tunnel for the interconnection IPSec configuration together static default routes are used. Crypto Maps are used to.
5 million bitcoin lost
Create an IPsec VPN tunnel using Packet Tracer - CCNA Security1. Keyring � 2. IKEv2 proposal � 3. IKEv2 policy � 4. Transform set � 5. Access list � 6. Define an IKEv2 profile � 7. Define the crypto map and. Trying to setup a site to site IPSec VPN between a Cisco ISR behind a NAT gateway (Fortigate) and Palo Alto located in Amazon Web Services. The. The IKEv2 key ring gets its VPN routing and forwarding (VRF) context from the associated IKEv2 profile. To configure type: crypto ikev2 keyring.